My very first CVE-2020-17476
There are several bug bounty platforms on the Internet like HackerOne and Bugcrowd with a lot of programs listed on them. These programs receive a lot of attention from bug hunters of various levels, as result - with time it becomes harder to find a bug, especially for beginners like me.
Fortunately not all bug bounty programs are listed on platforms, some companies prefer to drive programs on their own. And as soon as they should be discovered first, such programs receive less attention and more simple bugs survive.
Being a newbie I decided to look for such unlisted programs and managed to find some. Took one of them and started hunting.
In the bottom of the main page of the main domain there was a link to chat with support. I tried to open it among other things while browsing site and making myself familiar with it.
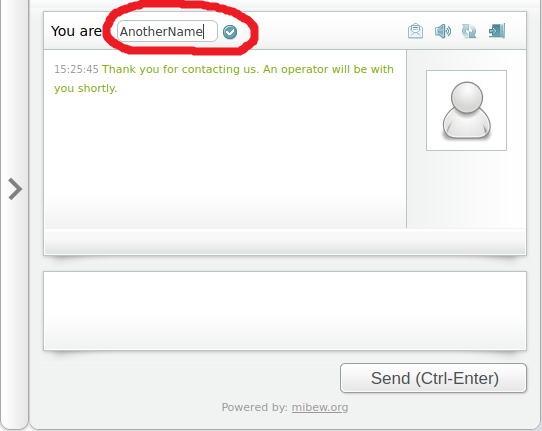
It was a regular chat except for one thing which took my attention. There was an ability for the user to change his name. Users can click on the name, input field appears and a new name can be entered.
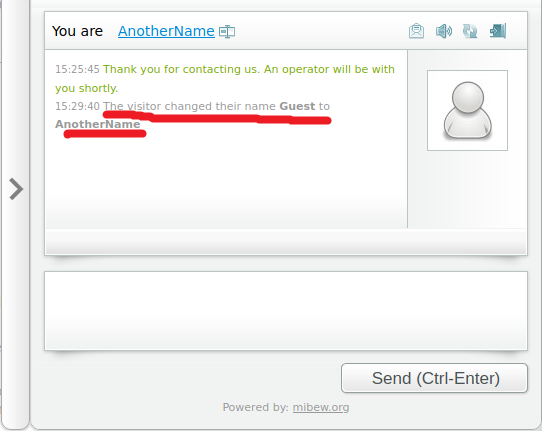
Then chat history shows: The visitor changed their name OldName to NewName.
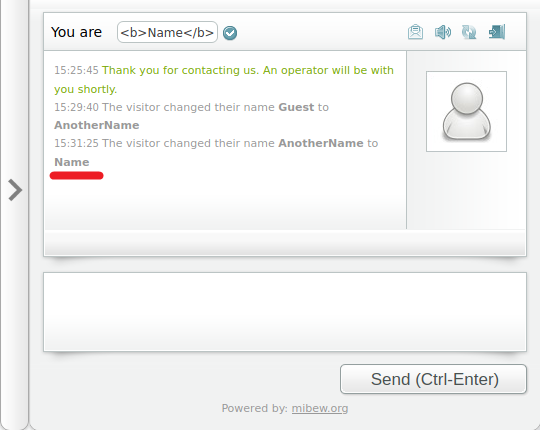
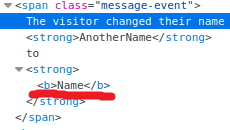
Smells like HTML injection. I tried to inject javascript with <script> tag and it was filtered out. Tried putting image with <img> tag and it didn’t appear either.
I made myself some coffee and started trying different tags. Finally I managed to find following payload: <a href="javascript:alert(document.domain)">X This results in big X which fires javascript on click.
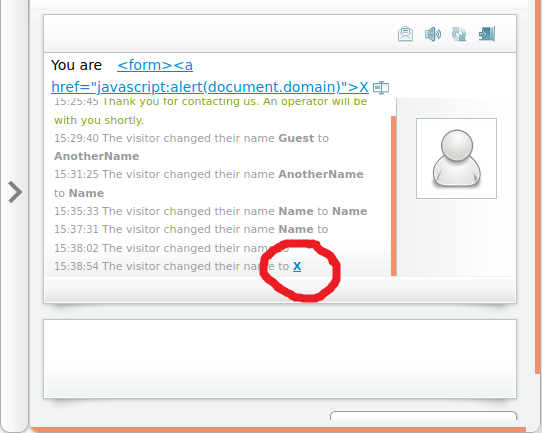
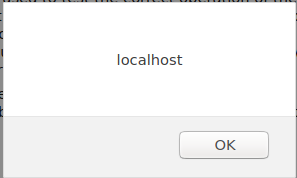
I checked how it looked on the chat operator’s side and X was there, javascript also was executed on click.
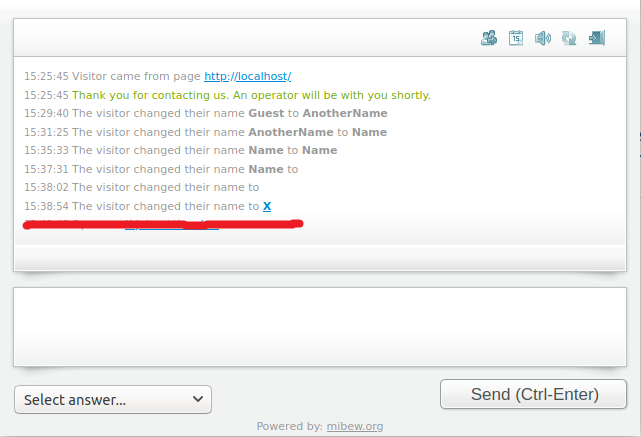
So, any unprivileged user can act on behalf of a chat operator in case the operator clicked a malicious link in the chat history.
I checked the chat page sources and found that it is Mibew Messenger. Googling showed that it is an open source project hosted at mibew.org.
I thought that issue could be present because of an outdated version installed, googled for such exploit but didn’t find anything. I have found that mibew.org has a demo of the latest version at https://mibew.org/ru/demo2, checked it and it was vulnerable. So, it turned out that I have found 0-day.
I contacted the vendor, he quickly confirmed XSS and published a fixed version in one day. They don’t have a bug bounty program but I got credit at https://mibew.org/credits (mentioned as adsec2s).
And also I used that chance to request my first CVE, it was assigned with CVE-2020-17476.